How to remove Dllhost.exe and Fix: COM Surrogate has stopped working (dllhost.exe)
Complete detail about COM Surrogate (dllhost.exe)
COM is basically known as the Component Object Model. This is a Microsoft GUI launched back in 1993 that enables designers to use a range of distinct programming languages to produce “COM items.” Essentially, these COM objects are plugging to extending other apps.
For example, when opening a folder, the Windows file manager uses COM objects to create thumbnail images of pictures and other files. To generate thumbnails, the COM object handles the processing of images, videos, and other files. This enables, for instance, the extension of File Explorer with assistance for fresh video codecs. And COM Surrogate is named “dllhost.exe,” as you might have imagined because the COM objects it hosts are.dll files.
There are several COM Surrogate procedures operating at the same time sometimes. You will usually see two of them working if you go to the task manager.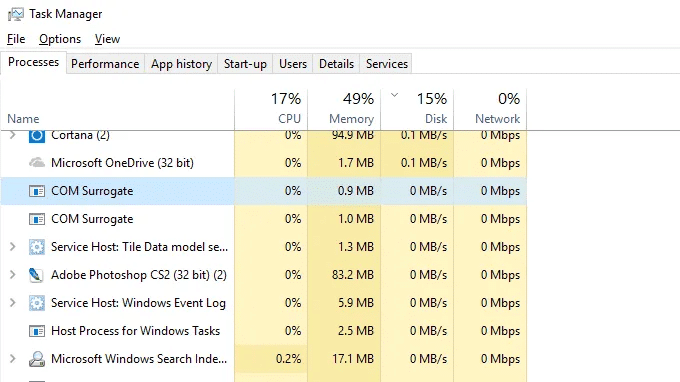
Fortunately, it isn’t a virus for COM Surrogate (most times). It’s a lawful, behind-the-scenes Windows 10 method. This is known as dllhost as the method is DLL files storage. This probably doesn’t make sense, so let’s clarify it in better detail.
Now that the COM object collapsed, the COM Supplement method would only be removed and the Explorer would proceed. Quite clever, right? You can actually view the COM item I am referring to above if you purchase Process Explorer.
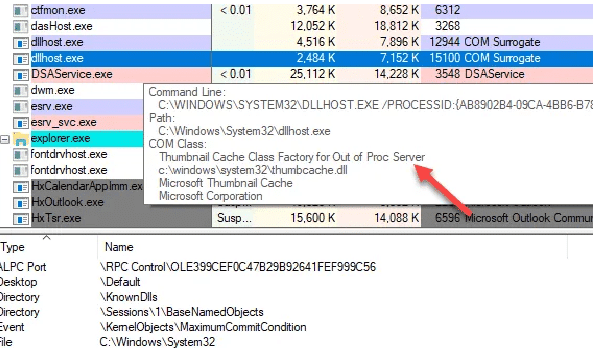
You can see the Microsoft Thumbnails Cache COM category, which is the Explorer expansion used to generate thumbnails if you hover your mouse across dllhost.exe section
DLLHOT.EXE * 32 COM Surrogate is known to be used by Trojan. EXE as a computer-infected method. You may have a trojan with your computer if you see a very big number of COM surrogate dllhost.exe * 32, with using a lot of CPU and RAM.
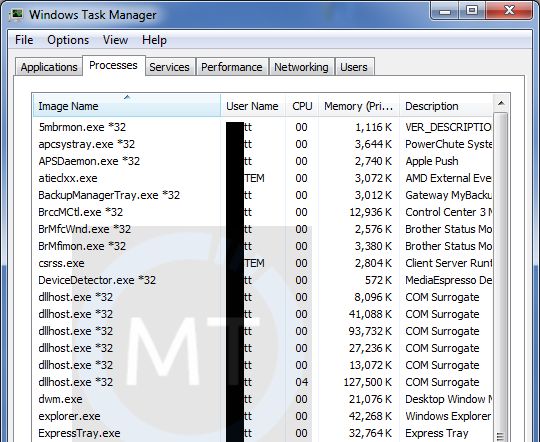
As dllhost.exe * 32 COM Surrogate is a popular system method, malware often disguises itself with a process title of “dllhost.exe * 32 COM Surrogate.” The original dllhost.exe * 32 COM Substitute system file is in the directory C:\Windows\System32.
Criminals can, however, hide Trojan people under the false copy of COM virus substitute. Indeed, it is the main characteristic of COM Trojan surrogate, the capacity to hide under the title of the lawful Windows method. Do not hesitate to take it from your scheme if you discover it in your task manager.
How do I explain which COM object is hosting a COM Surrogate?
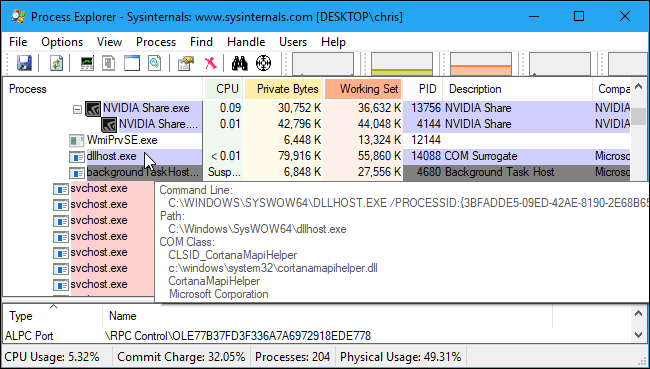
You can no longer find out what the COM object or DLL file a COM Surrogate procedure host on the default Windows Task Manager. We suggest the Microsoft Process Explorer tool if you want to see this data. To see which COM object or DLL file it host, download this method, then mouse over a dllhost.exe system in Process Explorer. This dllhost.exe is the host for the CortanaMapiHelper.dll object, as can be seen in the screenshot below.
Can we disable the COM Surrogate process
The COM Surrogate process can’t be disabled because it’s an essential component of Windows. This is a container method used to operate COM objects which other procedures are willing to run. For instance, Windows Explorer generates a COM Surrogate procedure frequently to produce thumbnails when you open a file. You can also develop your own COM Surrogate Processes for other programs you use. Another program, which does something the program wishes to do, has begun all dllhost.exe procedures on your machine.
Is COM Surrogate a virus?
In the past, Trojans and Viruses had masked themselves as COM Surrogate and other Windows processes in the Windows operating system. You can discover your original position if you open Task Administrator, right-click on the method and select Open file position.
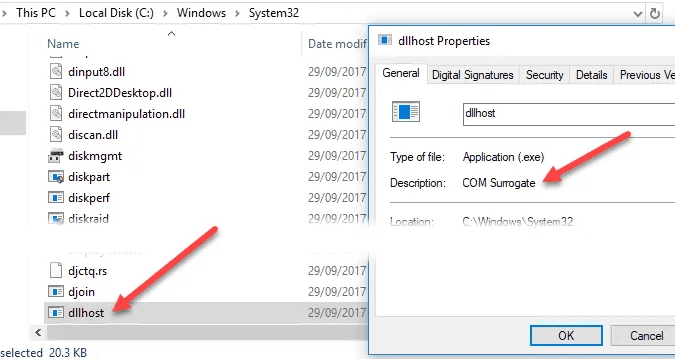
It is probable that a virus will be present if the COM Surrogate method leads to file ‘ dllhost ‘ within the directory C:\Windows\System32. You should scan a virus straight away if it goes elsewhere. COM substitute usually uses very little CPU and memory, and it only exists for one or two instances. I would recommend performing an offline bug test, which can better detect difficult hides bugs, if there are numerous dllhosts.exe procedures or if the method eats over 1 to 2% of your CPU.
Methods to remove COM surrogate virus
There are several methods to remove COM surrogate virus which are to be as follow as:
Method 1- REMOVE COM SURROGATE USING SAFE MODE WITH NETWORKING
One way to bypass Virus Helper items is to restore Windows with Networking into Safe Mode. Try an alternative method described below if that didn’t assist.
Step 1: Reboot your device with the help of Networking to Safe Mode.
- For Windows 7 / Vista / XP follow these-
1 Click on Start button then click on Shutdown then click on Restart then press OK.
2. Start clicking F8 various times when your desktop becomes active until you see the Advanced Boot Options window.
3. From the list, select Safe Networking Mode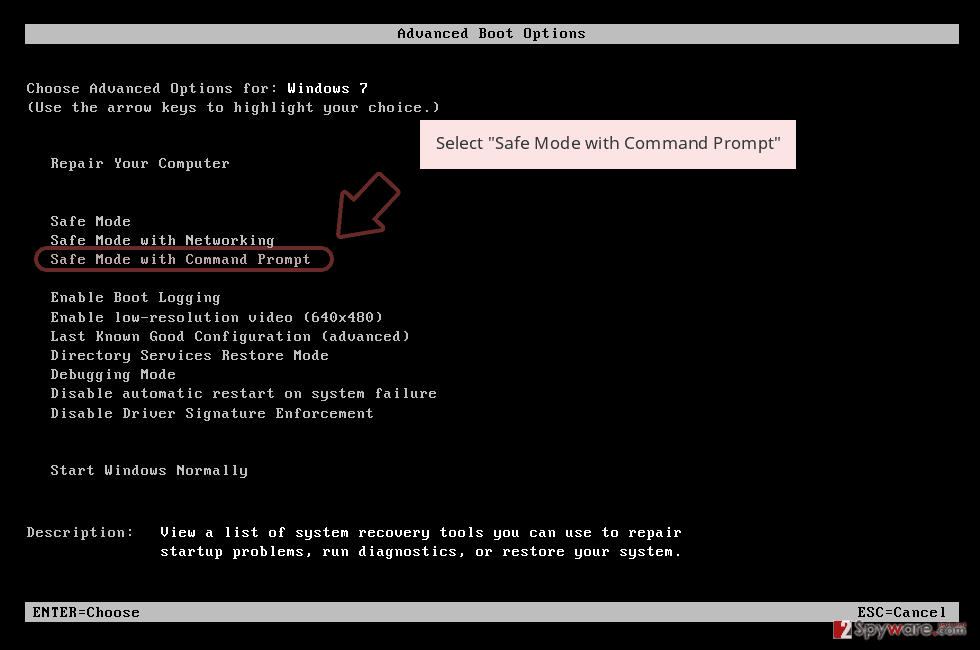
- For Windows 10 / Windows 8
1 On Windows Login Screen press Power key. Now press and hold the Shift key on your keyboard and click the Restart button.
2. Now select Troubleshoot then click on Advanced options then go to Startup Settings and finally press Restart.
3. Once your computer is active, in the Startup Settings folder, pick Enable Safe Mode with Networking.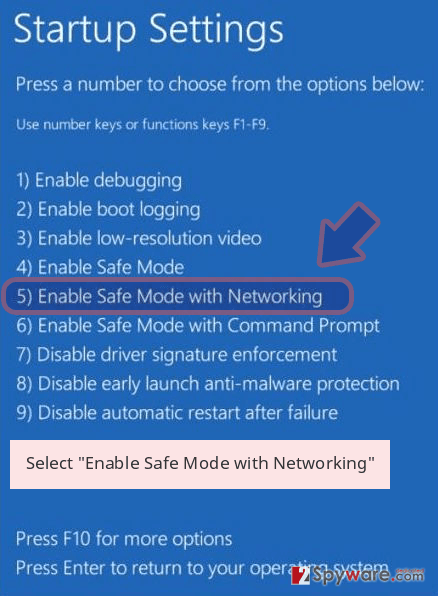
Step 2: Remove COM surrogate
Log in and begin the browser with your infected account. Download Reimage or any other lawful program for anti-spyware. Update before scanning a complete scheme and remove any malicious documents belonging to your ransomware and complete closure of the COM surrogate.
If blocking Safe Mode with Networking by your ransomware, attempt additional method.
Method 2 – REMOVE COM SURROGATE USING SYSTEM RESTORE
You can also use System Restore to get rid of COM surrogate virus steps are to be as follows as:
Step 1: Reboot your device to Safe Mode with the help of Command Prompt.
- For Windows 7 / Vista / XP follow these-
1 Click on Start button then click on Shutdown then click on Restart then press OK.
2. Start clicking F8 various times when your desktop becomes active until you see the Advanced Boot Options window.
3. From the list, select Command Prompt.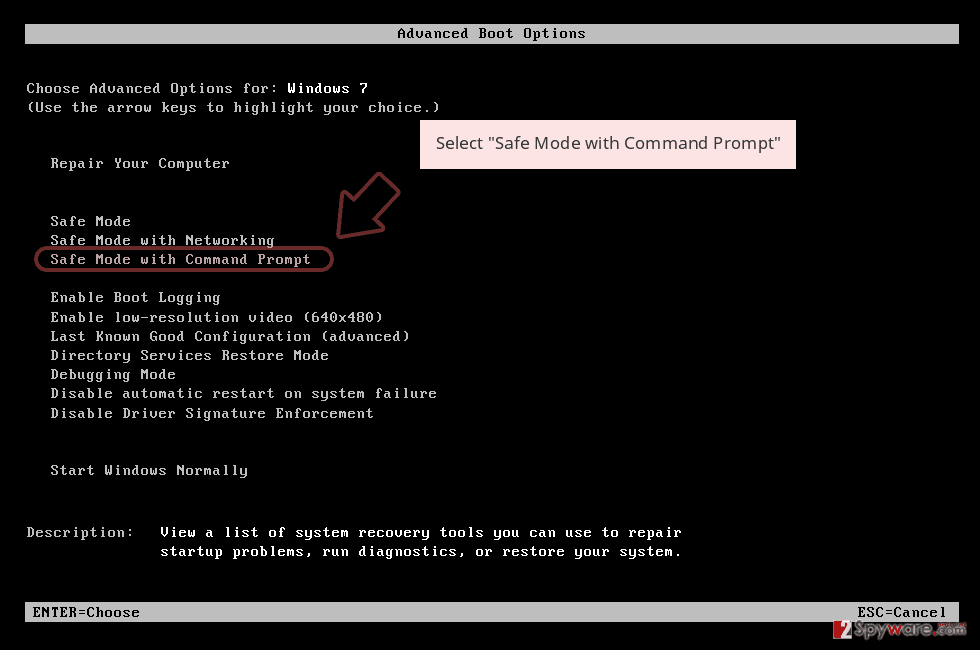
- For Windows 10 / Windows 8
1 On Windows Login Screen press Power key. Now press and hold the Shift key on your keyboard and click the Restart button.
2. Now select Troubleshoot then click on Advanced options then go to Startup Settings and finally press Restart.
3. Once your computer is active, in the Startup Settings folder, pick Enable Safe Mode with Command Prompt.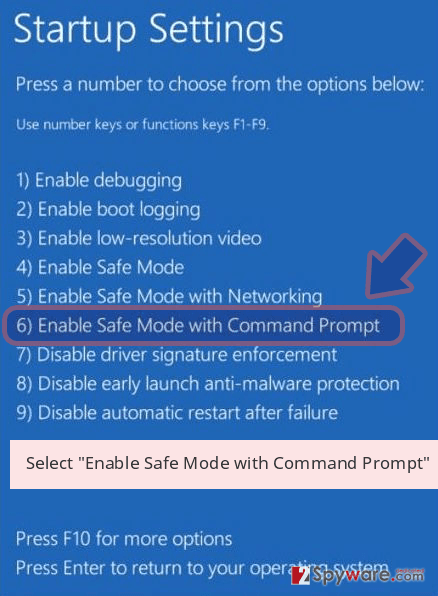
Step 2: Restore data and configurations of your computer.
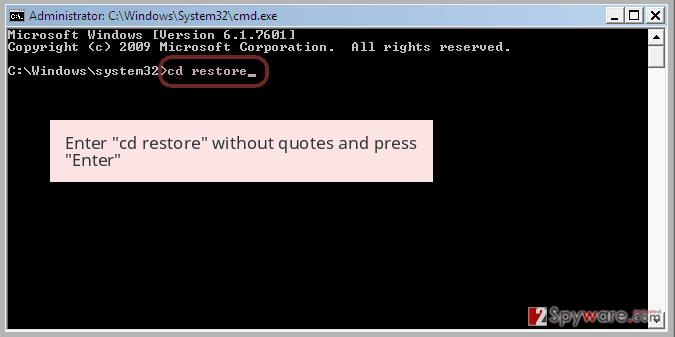
- Once the Prompt command window appears, enter the cd restore and press Enter.
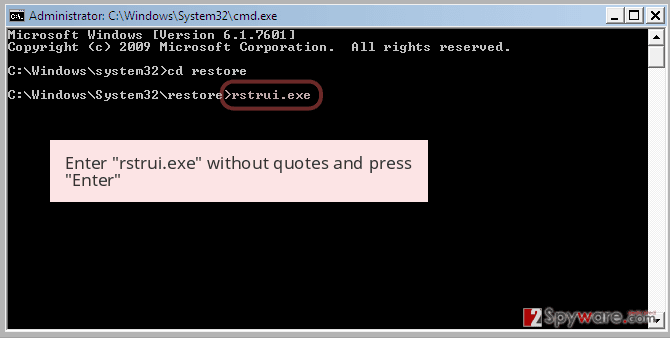
- Type rstrui.exe now and again press Enter.
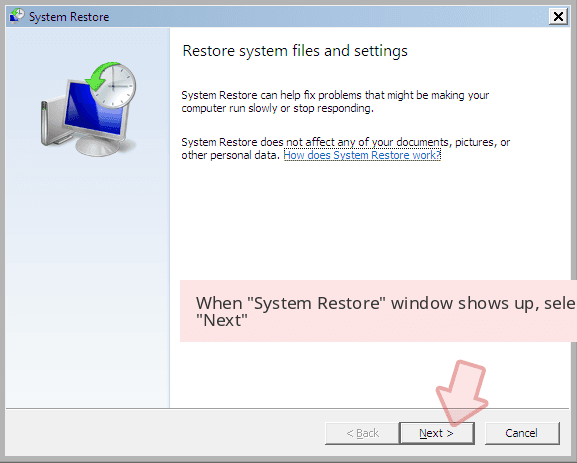
- Click Next when a fresh window appears and pick your restore point prior to COM surrogate infiltration. Click Next after doing this.
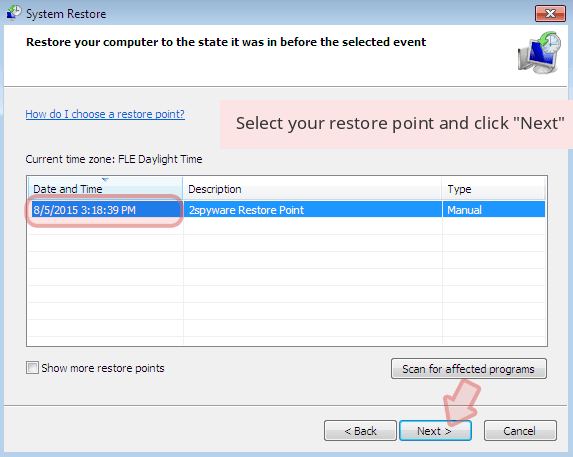
- Now click Yes to recover the system.
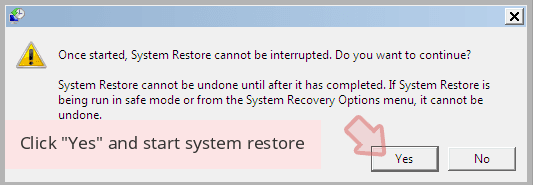
Once you have restored your device to a prior date, download and scan your laptop with Reimage and ensure successful extraction of COM surrogate.